Trusted by global leaders for fast, reliable endpoint








Identify attackers in days, rather than weeks or months
Faster investigation and reduced response times with forensic tools
30% faster recovery time post breach

Operations across Asia, USA, Japan, and Australia.

Protects global defense agencies with awarded research contracts.

Founding members behind Fortune 500 security testing.

Expert-built with flexible, cost-effective pricing.

Featured at hackathons and secured Fortune 500, defense, and fintech programs.

Try it free with no strings attached.
1% CPU usage with low-impact, continuous monitoring

Turns endpoints into decoys to expose attackers

Deploys fake services, processes, and credentials

Verifies identities for policy sign-ups and claims

Protects loyalty points from fraudsters

Alerts unusual logins and enforces extra checks
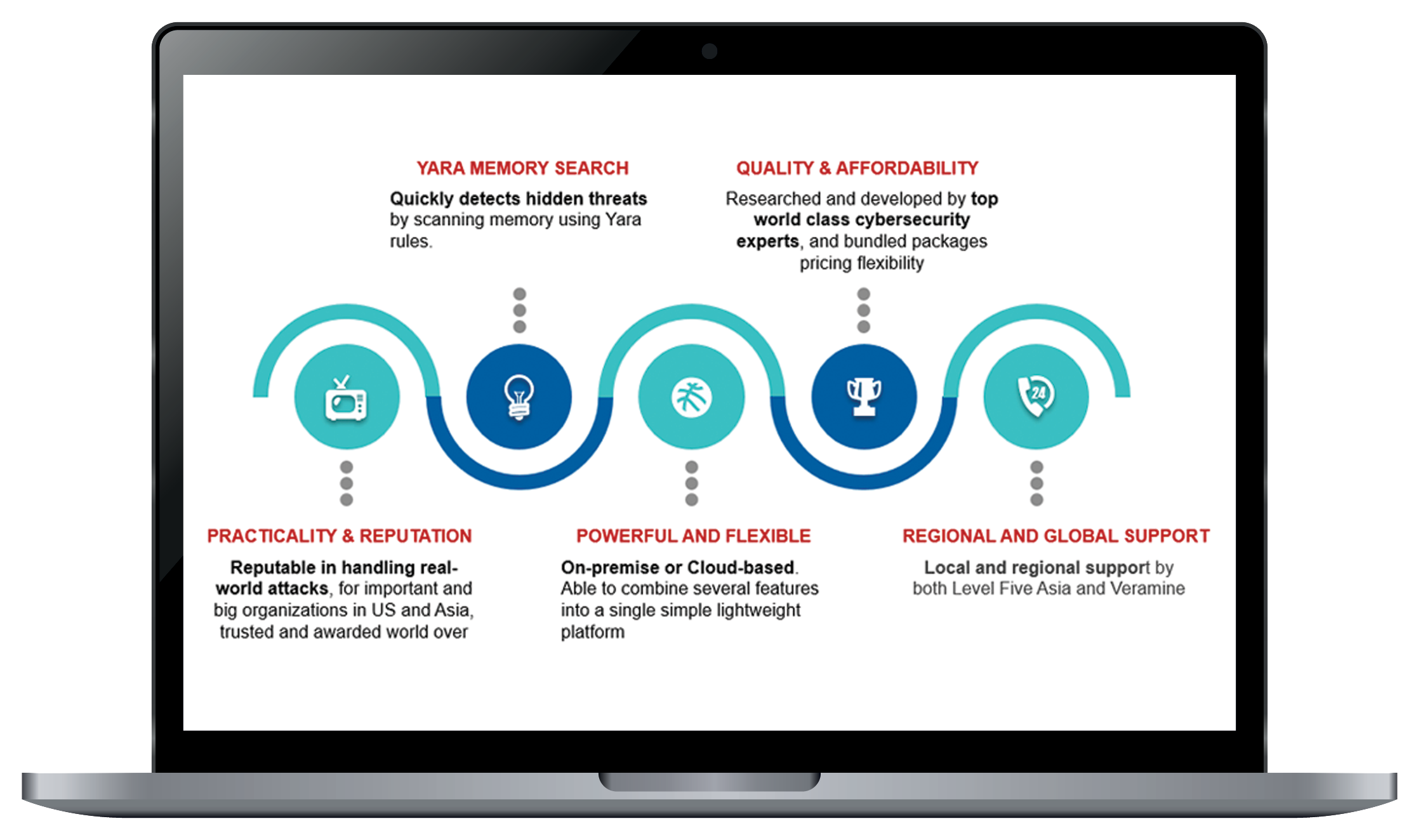

Finds hidden malware using Yara memory scans

Spots suspicious activity like strange commands and IPs
Auto-resets passwords after a breach

Blocks confirmed threats using threat intel
Stops password theft tools like Mimikatz

Search past and real-time data to find threats fast

Isolate, block, and remove infected users, files, and devices
Tracks user activity, keystrokes, emails, and USB use