Incident Response: 8 Steps To Take After A Breach

Credential-based cyberattacks are on the rise—where attackers steal login credentials to infiltrate systems, exfiltrate sensitive data, or impersonate users. Whether it’s through phishing, brute-force attacks, or dark web credential leaks, once a breach occurs, your response in the hours and days that follow is critical.
The steps outlined below are grounded in best practices to contain the damage, minimize the damage, and fortify your defenses moving forward.
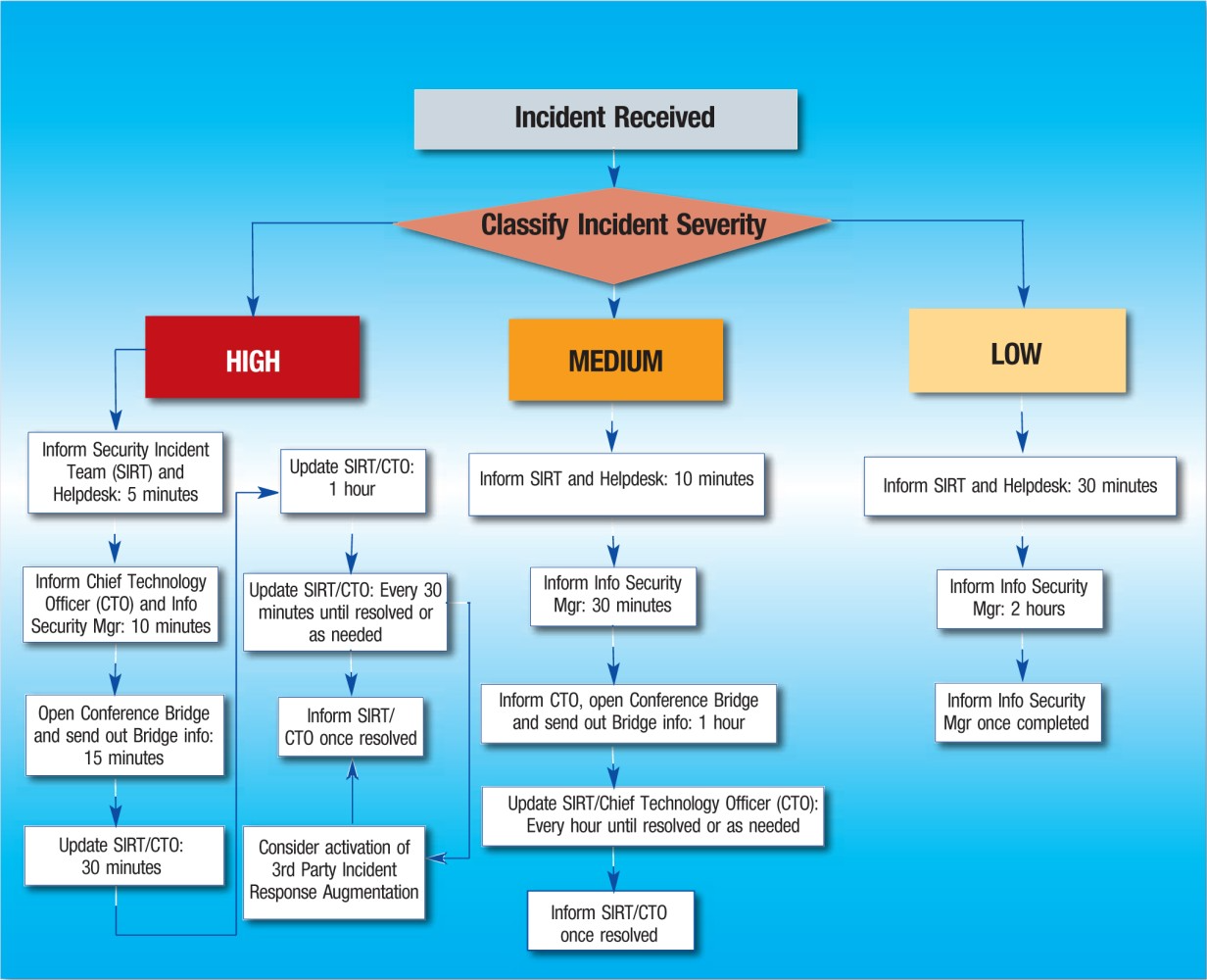
1. Confirm the Breach and Contain It Immediately
When you suspect a breach, act quickly—but don’t panic. The first step is to confirm the compromise by analyzing logs, security alerts, and anomalies in user behavior. Once confirmed:
- Isolate affected endpoints or servers from the rest of the network.
- Disable compromised accounts immediately.
- Revoke session tokens and temporary access rights.
- Ensure any lateral movement is stopped to prevent the attacker from reaching other systems.
Containment must be done without destroying evidence, as you’ll need it later for forensic analysis.
2. Mobilize Your Team
Every organization should have an incident response (IR) plan tailored to its environment. If you haven’t developed one yet, now is the time to build it into your process moving forward.
For those with a plan:
- Mobilize your IR team, including IT, security, legal, HR, and communications personnel.
- Initiate predefined workflows and assign clear roles and responsibilities.
- Ensure all activities, findings, and decisions are thoroughly documented for post-incident review and compliance.
3. Investigate and Analyze the Attack
Once the breach is contained, conduct forensic investigations to determine the root cause and scope of the incident. This includes:
- Identifying how attackers gained access (e.g., phishing email, credential stuffing).
- Pinpointing which systems were accessed and what data may have been exfiltrated or modified.
- Searching for persistence mechanisms the attacker may have established (e.g., backdoors, malicious scripts).
You may want to work with cybersecurity firms or forensic specialists to support this step and provide an unbiased, thorough assessment.

4. Reset Credentials and Secure Access Controls
With compromised credentials at the heart of the breach, resetting and securing access is paramount:
- Enforce mandatory password changes for all users—especially high-privilege accounts.
- Implement or review Multi-Factor Authentication (MFA) across your network and SaaS platforms.
- Decommission unused accounts and adopt least privilege principles.
- Update access logs and monitor for any attempts to reuse stolen credentials.
Remember, restoring access isn’t just about locking the front door, it’s about checking for open windows too.
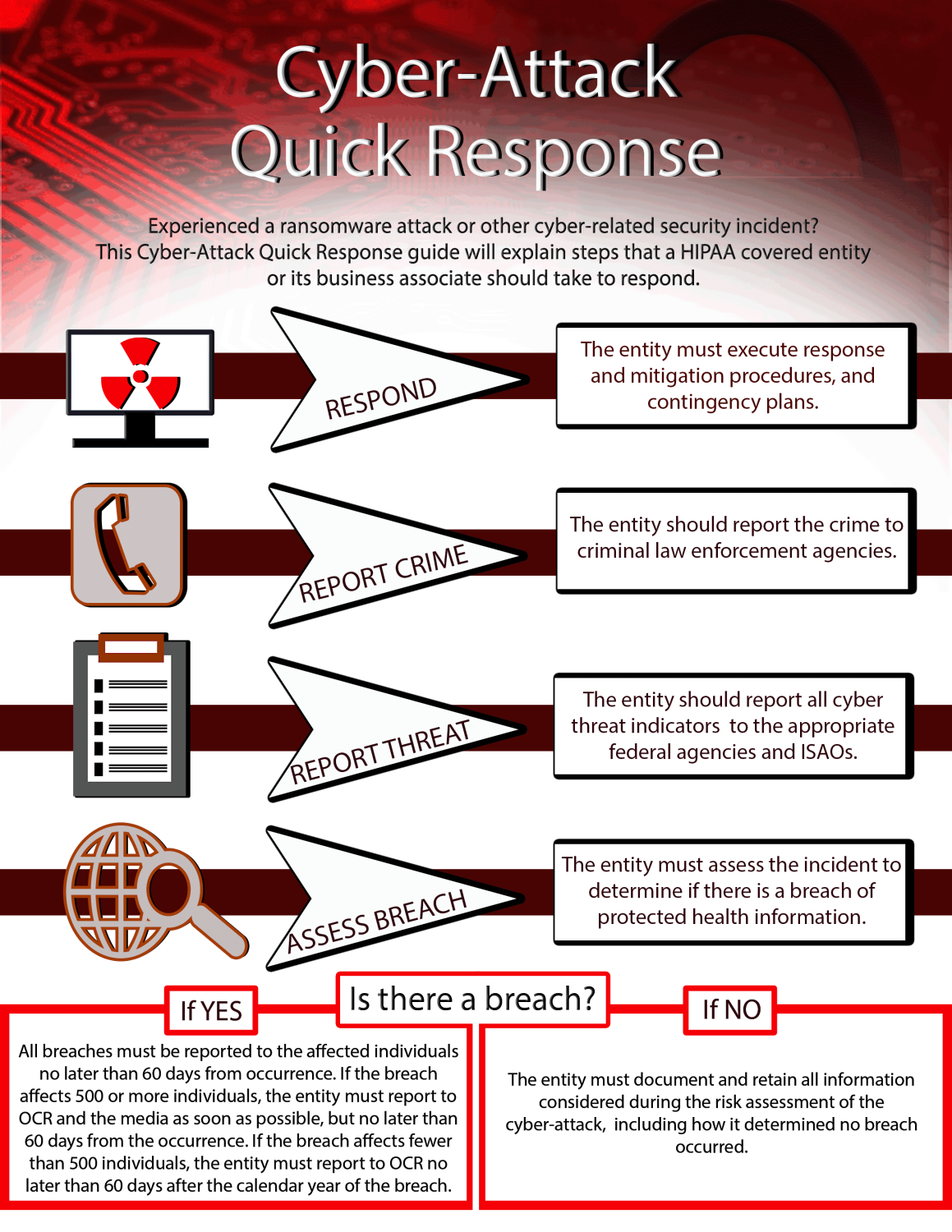
5. Notify the Right Stakeholders
Depending on the severity and scope of the breach, your organization may be required to notify:
- Regulatory authorities (GDPR, HIPAA, PCI-DSS, etc.).
- Impacted customers or employees, particularly if personal data was accessed.
- Third-party vendors or partners that may be affected or integrated with your systems.
Transparency is critical. Provide accurate information on what happened, what data was involved, and how you’re responding to the situation.

6. Remediate and Fortify Systems
Recovery doesn’t immediately mean “back to business”. Rather, it’s a chance to fix the underlying issues. Post-attack remediation involves:
- Applying patches to vulnerable software or misconfigured systems.
- Updating firewall and endpoint rules.
- Re-evaluating user permissions and access policies.
- Segmenting networks to contain future incidents more effectively.
Consider adopting an assume breach mindset by building controls that minimize the blast radius if an attacker does gain access.

7. Review Security Culture
Most breaches (up to 95%) are the result of human actions. Credential breaches often start with user error, such as clicking on a phishing link or using weak passwords. Strengthen your human firewall by:
- Conducting phishing simulations and mandatory security training.
- Promoting awareness of social engineering tactics.
- Reinforcing good password hygiene and safe data practices.
Your staff can be your greatest asset or your weakest link. Make cybersecurity part of the culture, not just compliance.
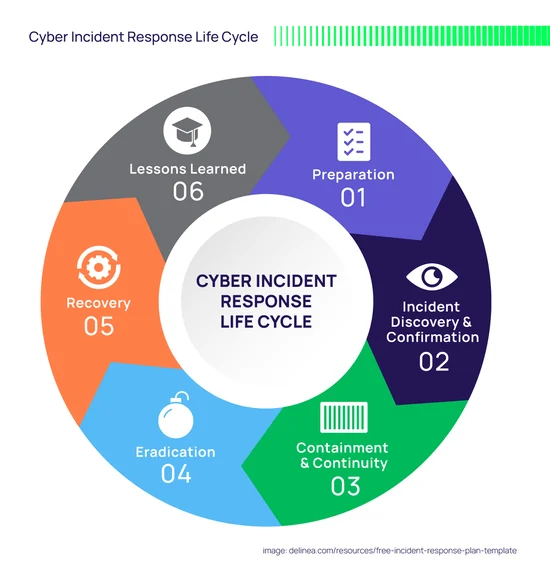
8. Review and Improve Your Incident Response Plan
Once the dust settles, conduct a post-incident review to:
- Identify what worked and what didn’t in your response.
- Adjust IR playbooks to address any gaps.
- Update security policies and refine escalation paths.
- Consider testing your response plan through tabletop exercises and red teaming.
Use the incident as a learning opportunity to become more resilient. Recovery doesn’t stop when the systems are back online—it continues as you evolve your approach to risk and response.
Closing Thoughts
Breaches are common in some industries, but how you respond is how you mitigate the impact of the attack. The way you respond to a breach can demonstrate your organization’s resilience, maturity, and commitment to safeguarding both your operations and your stakeholders.


