5 Sinister Ways Attackers Can Damage Your Hardware

When we think of cyberattacks, we often picture stolen data or compromised accounts. But did you know that cyber attackers can also target your hardware, aiming to damage or permanently disable it? From malicious software tricks to dangerous USB devices, here’s how attackers might destroy hardware—and what you can do to stay protected.
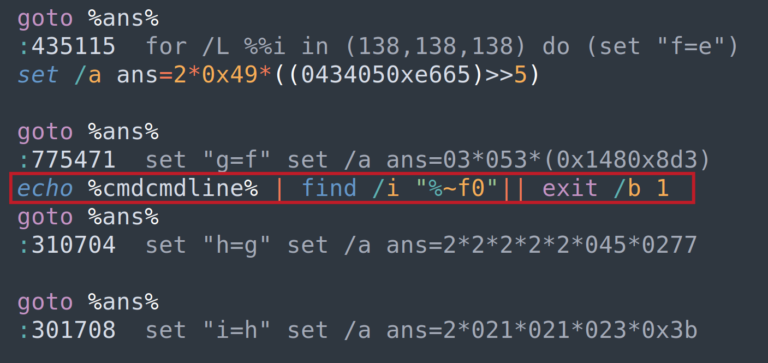
1. Batch File Obfuscation: Hiding Malicious Commands
Batch files are simple text files that execute a sequence of commands in Windows. But attackers use batch file obfuscation to hide malicious intent. By disguising destructive commands (like formatting drives or deleting system files) inside complex scripts, they evade detection and trick users into running them. One wrong click could wipe critical files or render your system unbootable.
🛡️ Protection Tip:
- Avoid running unknown .bat or .cmd files, even if they come from trusted-looking sources.
- Use reputable antivirus solutions that scan scripts for obfuscated code.
- Enable Windows’ built-in execution policy restrictions to limit the running of unsigned scripts.
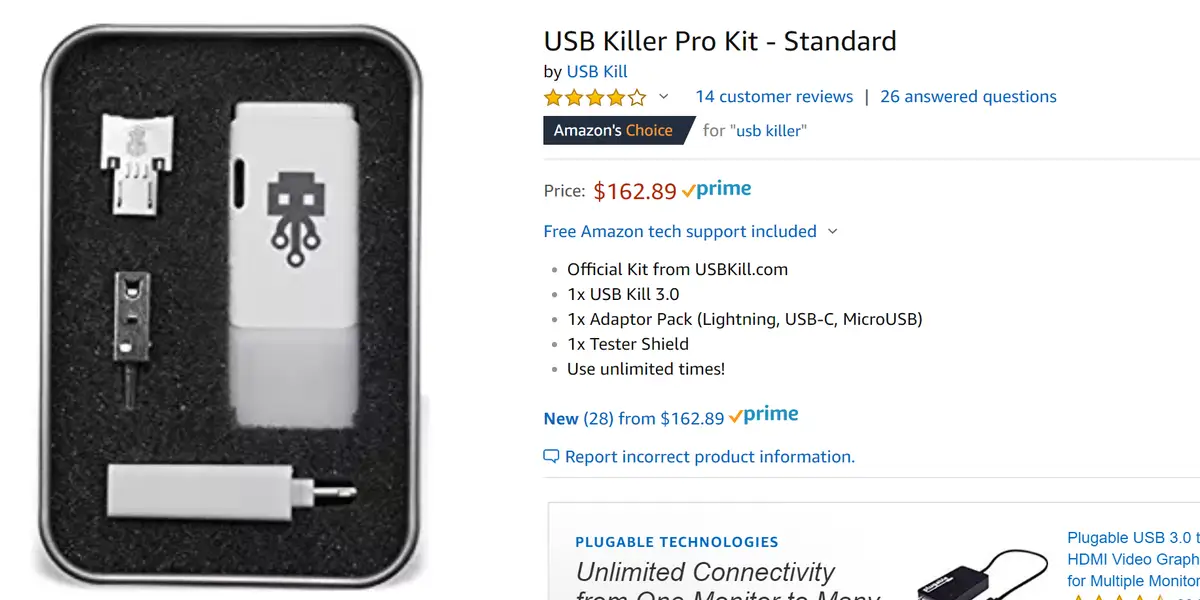
2. USB Killer: Physically Frying Hardware
Unlike the above software attacks, the USB Killer is a physical device that looks like a normal USB drive but delivers high-voltage electrical surges through the USB port once connected. These surges can damage or destroy your motherboard, USB controllers, and connected components in seconds.
🛡️ Protection Tip:
- Never plug in unknown or found USB devices.
- Consider using USB data blockers (USB condoms) to prevent electrical transmission when connecting to unknown ports.
- Disable unused USB ports via BIOS or device manager if not needed.

3. The Zip Bomb: Crashing Systems with Compression
A zip bomb is a cleverly crafted compressed file designed to unpack into billions of gigabytes of data. When an antivirus or file scanning software tries to decompress it, it can overwhelm memory and processing resources, leading to crashes or freezes. While not a direct physical attack, it causes denial-of-service and potential file system corruption from forced shutdowns.
🛡️ Protection Tip:
- Avoid downloading zip files from unknown sources.
- Configure antivirus tools to limit decompression depth or file size.
- Stay updated on security patches that mitigate decompression vulnerabilities.
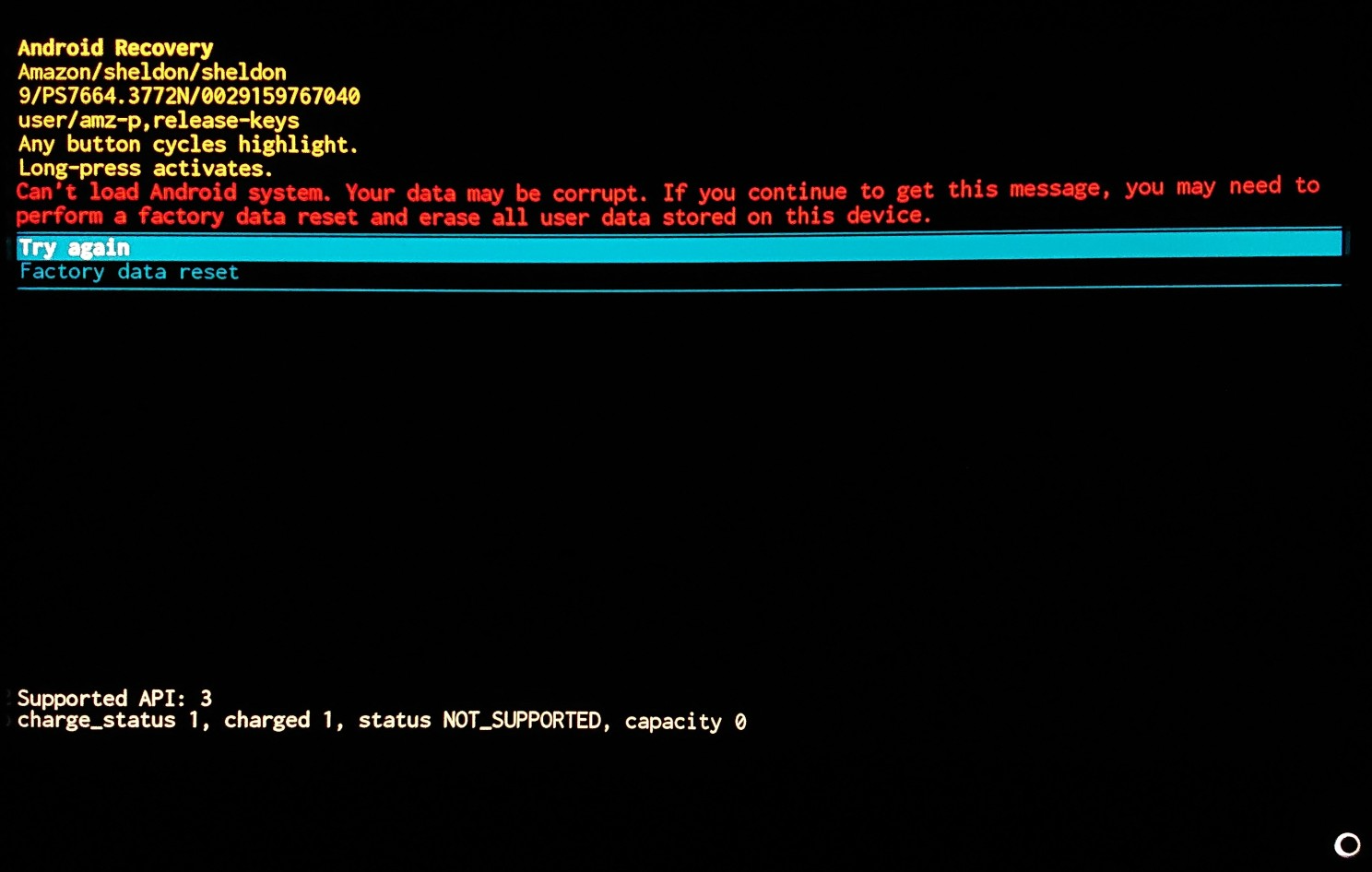
4. Bricking Attacks: Rendering Devices Unusable
“Bricking” refers to turning a functioning device into a useless “brick.” Attackers can corrupt your system’s firmware or bootloader, preventing it from booting. This can be achieved through malicious firmware updates or low-level software exploits. Once bricked, the device may require specialized equipment or professional servicing to recover—if recovery is even possible.
🛡️ Protection Tip:
- Only install firmware or BIOS updates from official sources.
- Enable secure boot features in your BIOS.
- Keep hardware write-protected where applicable (e.g., router firmware locks).

5. Rowhammer: Flipping Memory Bits
Rowhammer is a hardware-based attack targeting DRAM memory. By repeatedly accessing (“hammering”) specific rows of memory, attackers can induce bit flips in adjacent memory cells, leading to data corruption, privilege escalation, or system instability. On vulnerable systems, this can undermine hardware-level integrity without any physical contact.
🛡️ Protection Tip:
- Use systems with Rowhammer-resistant memory (ECC RAM).
- Keep device firmware updated to incorporate mitigation techniques.
- Use memory integrity features provided by your operating system.
🔒 Staying Ahead of Hardware-Damaging Threats
While these attacks range from physical to purely digital, they highlight the growing convergence of cybersecurity and hardware security. The best defense lies in a combination of vigilance, updated systems, and physical security controls.
In summary:
- Never plug in unknown devices.
- Don’t execute suspicious files or scripts.
- Update software and firmware regularly.
- Use security settings (like Secure Boot, restricted USB access) to limit exposure.
Cyber attackers are constantly trying out new methods—and we should always be prepared.


